

Data breach. In this ever-connected world, those words conjure fear, and rightly so. Click on an innocent-looking email, webpage URL or attachment, and the next thing you know, someone has access to your email or your company’s confidential files. Perhaps someone decides to hold your data hostage with ransomware. Regardless of how it happened, and it will eventually, there are certain things an organization’s communications team need to keep in mind.
Lawyers Are Your Friends
I know what you’re thinking: Is there any organization where PR and legal have not disagreed on strategy for communicating during a crisis? If so, I’d like to learn their secret.
In a data breach, lawyers are PR’s friends. But first, the necessary disclaimer. This article is not legal advice. I am not a lawyer, though I’ve worked with many. Still, if you rely solely on this article to guide you through a data breach, or any other potentially legally damaging event, then you will be missing out on useful legal advice.
The State of Pay...
Here’s why communications and legal should be joined at the hip during, and after a data breach.
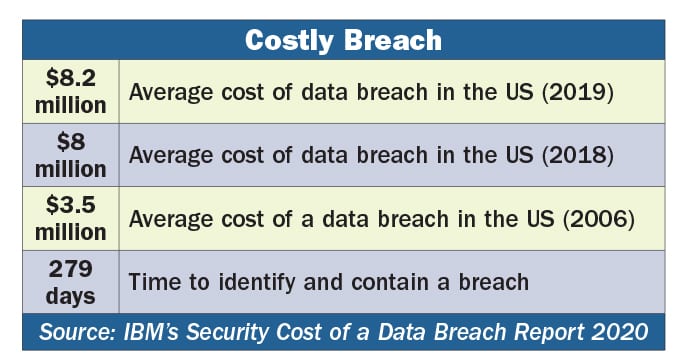
First, and probably most important, data breaches can be expensive. Really expensive. Not only are there costs associated with containment and repairs—think IT and new software patches or security upgrades—but regulatory agencies take a dim view of big data breaches. Often this leads to costly fines and settlements.
In addition, there are indirect and hidden costs, respectively, associated with data breaches, including reputation damage (indirect) and lost business (hidden), the latter of which usually is the largest cost.
Remember the huge Equifax breach of 2017? The company settled with the Federal Trade Commission (FTC) for $575 million. All told, Equifax in 2019 agreed to pay out $700 million to settle federal and state fines and penalties.
As we went to press last month, Equifax set aside another $100 million for breach-related penalties. Incidentally, this does not include the company’s legal or professional services expenses.
It also does not include $337 million Equifax spent in 2019 on technology and data security, legal and investigative fees, and product liability for the breach, according to Housingwire. All told, the breach has cost Equifax $1.7 billion.
...And Pay the State
Not only are federal and international regulators in the breach-punishment business. Similarly, states have a patchwork of data breach laws and notification requirements.
For example, the California Consumer Privacy Act (CCPA), which went into effect January 1 (see PRNEWS, Nov. 2019) requires businesses to maintain “reasonable security procedures and practices.”
What that means is not clear yet, but penalties for violating CCPA data security requirements are steep: $100 to $750 per consumer, or actual damages, whichever is higher. Add up how many customers you have in CA and the number gets big quickly.
Internationally, the fines are big too. Under the European Union’s General Data Protection Regulation(GDPR), breaches that cause “a high risk of harm to the rights and freedoms of natural persons” can result in fines worth millions, even if your company is not based in the EU.
With the possibility of these high fines, the advice is to set up a coffee with your general counsel. Use the session to build a relationship, or enhance it. Also, during the coffee, strategize about how to deal with data breaches. Perhaps this means creating pre-approved communications instruments that are ready asap after a breach is discovered.
Whom to tell, and What to Say
To say there is great variance between US states on whom, how and when to notify individuals affected by a data breach is an understatement. In addition, those requirements change frequently.
Look at three examples:
In Indiana, data covered by breach regulations is straight- forward. It includes first and last name, or first initial and last name, coupled with driver’s license number or state identification number, credit card number or financial account with the code to access it. Here is one area where Indiana differs; if a breach touches just one single state resident, you must inform the attorney general, who can take subsequent action and require further notifications.
In Texas, breach data is defined similarly to Indiana but also includes health information. If more than 250 state residents are impacted, you have to notify the Attorney General.
In New York, if it’s a breach that would cost more than $250,000 to notify those impacted, a statewide media release can be substituted.
Requirements like New York’s are why you see press re- leases for large data breaches, especially when the universe of those impacted and the scope of the damage might not yet be clear. Many states require that a notice go out without reasonable delay. In other words, unless your organization is large enough to have in-house data breach notification processes and is up-to-date on the shifting requirements of state breach laws, you are going to need outside help.
The Role of Communications
Communicators often craft messages to consumers, work with legal on press materials and set up a process for handling the inevitable breach-related customer service issues.
Typically, customers are displeased with the letter they receive or the story they see on the evening news. Your role is to help educate customers on what they can do to protect themselves and what your company is doing to make sure the breach doesn’t recur. Having read more than a few post-breach letters to consumers, I can’t overstate the need to employ plain, easy-to-read language and a sympathetic tone.
What to Do After a Breach
Consumer trust in brands is critical to their value and to the companies behind them. Some, if not all, customers consider a data breach as a loss of trust; I gave you my personal information and you didn’t keep it safe. There is no quick, sure-fire way to fix the damage to reputation that a data breach can cause.

However, there are steps for communicators. Just as in crisis scenarios, it’s advisable to tell the public:
- What you know, within limits, if there is an ongoing criminal investigation;
- What you can do to help (offer credit monitoring, for example); and
- What you are doing to fix the problem and learn from it.
These are obvious steps that will help in securing the business and controlling reputation damage.
With a breach, full disclosure of facts is, in many cases, not an option. You don’t want to give hackers an idea of how to hurt you again.
On the other hand, communicating promptly and clearly that you understand how your customer feels (victimized) can go a long way in limiting reputation damage.
Training and Preparation for Staff
The world’s best data security software can’t protect your organization from human error. One of the best ways to prevent data breaches is through training.
Of 4,200 security incidents reported in 2019, nearly 3,000 were due to negligent or inadvertent employees, IBM’s Security’s Cost of Insider Threats: 2020 Global Report says.
You, as a communications professional, can help explain that to internal audiences who need training, and to executives, who may not want to pay for it.
Stress that this is not a boring compliance seminar that staff can surf the internet to learn. It is serious material with real-world financial consequences if done incorrectly.
Incidentally, bolster your argument with financial statistics from The Ponemon Institute, which discovered that deploying an incident response team and having an incident response plan reduced costs by $350,000 per breach.
There are companies that offer online training courses to help maintain good security (e.g. don’t use “password” as a password and never click on an attachment from someone you don’t know).
I’m familiar with KnowBe4 from using some of its training materials. This is not an endorsement, only an expression of first-hand knowledge. Your IT department, no doubt, knows numerous companies with various products to educate your teams on the crucial need for good data security.
Federal Resources
There are also resources from the FTC and other federal agencies. For example, the FTC’s Cybersecurity for Small Businesses, available at ftc.gov, is a good place to start if you’re not sure what your company needs to do.
The Department of Homeland Security’s Cyber-Infrastructure Security Agency also offers a variety of tools and processes to dig into your security structure and identify problems. If you use these it will fall to you to explain why they are important, and how your teams should take these trainings and process evaluations seriously.
Play Like You Practice
I know, this might seem a depressing topic given that everything today is interconnected and it’s so easy for it all to come crashing down because an intern clicked on a phishing email, exposing your whole IT structure.
I won’t lie; data breaches are awful. They are time-consuming to prepare for, respond to and fix. The key components are preparation and training. It’s a cliché because it’s true: you play like you practice.
If your data breach response plan is in a notebook on a bookshelf covered in dust, you are unprepared. The day you learn of a breach is not the time to schedule data security training for your people; it was last month or last year. It’s always better to have a story to tell regulators about your training and security practices than no story at all.
CONTACT: s_e_payne@hotmail.com
